Modernizing Third Party Risk Management with AI
A Comprehensive Guide
Introduction: Why Third Party Risk Is Everyone’s Problem
Few business leaders doubt that digital ecosystems have become essential to delivering products and services. Banks rely on fintechs and cloud providers; manufacturers depend on logistics firms, component suppliers and software vendors; and retailers build experiences on a patchwork of marketing agencies, payment gateways, and data brokers. Vendors help organisations scale quickly and access innovation, but each dependency introduces risk.
A single compromised supplier can cascade into operational downtime, regulatory fines, or reputational damage. Studies have shown that third‑party breaches are growing faster than direct attacks; according to a 2025 security forecast, more than 60 percent of companies suffered a third‑party data breach and attackers increasingly target high‑profile industries. The number of privacy and cyber‑security laws is rising, and regulators are tightening requirements for how organisations oversee vendor relationships, from the U.S. Interagency Guidance on Third‑Party Relationships to Europe’s Digital Operational Resilience Act (DORA) and the upcoming EU AI Act.
Despite this complex risk environment, many vendor risk programs still rely on static, point‑in‑time assessments. Teams send lengthy questionnaires once a year, review security certifications, and sign off until the next cycle. While these approaches may satisfy historical audit requirements, they do little to protect the organisation between audits. Suppliers can change systems, fall behind on compliance, or suffer a breach without notice. Mergers, geopolitical events, social issues and natural disasters further alter the risk profile. As one industry analyst noted, static risk assessments cannot keep up with the dynamic nature of modern supply chains and will become obsolete.
This guide explores how organisations can modernise third‑party risk management (TPRM) by moving from periodic assessments to continuous, real‑time monitoring, powered by artificial intelligence (AI), machine learning (ML) and natural language processing (NLP). The article is written in the style of a professor explaining concepts to students: authoritative yet conversational, with examples, analogies and supporting evidence. It draws on regulatory guidance from North America, Europe, the UK and Australia; case studies of companies using generative AI for due diligence; and predictions from industry analysts. The result is a comprehensive roadmap to help risk managers, procurement leaders, compliance officers and technologists design TPRM programs that are scalable, resilient and aligned with evolving legal and ethical expectations.
To set the tone, the following image conveys the complexity of modern digital supply chains. Nodes and connections suggest the interwoven relationships that risk managers must oversee, while the futuristic colours evoke the role of advanced analytics and AI in taming this complexity.

Complex digital supply chain network
Figure 0: Abstract representation of a complex digital ecosystem, symbolizing the interconnected networks of third‑, fourth‑ and Nth‑party relationships that modern organisations must manage.
Why Static Assessments Fall Short
1.1 The Illusion of Annual Questionnaires
For decades, risk managers have sent vendors questionnaires covering topics like information security, data privacy, business continuity, and financial health. Vendors respond with policy documents, security certifications (ISO 27001, SOC 2), and self‑attestations. These questionnaires are often long and generic, leading to “tick‑box” answers that do not reflect the vendor’s real‑time posture. Once the assessment is done, it may be twelve months or more before anyone asks again.
This model fails for three reasons:
- Rapidly changing threat landscape. Cyber‑attacks, regulatory fines, supply chain disruptions and ESG controversies can emerge overnight. An annual review cannot catch vulnerabilities that arise weeks or days after the last questionnaire. For instance, a supplier might lose a critical subcontractor or misconfigure a cloud service, creating new exposures that remain undetected until the next cycle.
- Complex multi‑tier supply chains. Organizations rely on fourth, fifth and Nth‑party providers, meaning your vendor’s vendors (and their vendors) might handle your data or operations. A recent analysis noted that the greatest challenge is simply identifying relationships beyond direct vendors. Without visibility into this extended network, concentration risk where many suppliers depend on the same subcontractor or region can go unnoticed.
- Static data cannot capture dynamic risk signals. Financial health, regulatory compliance and ESG posture can all change quickly. Traditional assessments rarely include up‑to‑date news, social media signals or real‑time performance metrics. They therefore miss early warning signs of supplier distress, such as declining revenue, sanctions, adverse media or social unrest.
1.2 Growing Pressure from Regulators and Stakeholders
Regulators now expect organizations to monitor third parties continuously and ensure resilience. The U.S. Interagency Guidance on Third‑Party Relationships stresses that monitoring is integral throughout the life of the relationship; it should confirm that controls remain effective, provide timely escalation of issues like security breaches or service interruptions, and adapt frequency based on risk. The guidance lists factors to monitor, including changes in financial condition, compliance lapses, subcontractor oversight, and external conditions such as geopolitical events. Similarly, Europe’s DORA requires continuous monitoring of third parties across financial, ESG, cyber and data‑breach risks, including mapping fourth‑party dependencies and maintaining a central register with breach histories. From 1 January 2025 in the UK, new rules for critical third parties (CTPs) will compel designated providers to undertake resilience testing, report incidents and provide assurance to regulators.
Australia’s APRA CPS 234 demands that financial institutions maintain an information security capability commensurate with threats, implement controls, test them systematically and notify regulators of material incidents. Taken together, these requirements signal that static, annual questionnaires are no longer sufficient; regulators expect ongoing, risk‑based monitoring.
Stakeholders are also raising expectations. Consumers, investors and employees increasingly ask about supply‑chain ethics, environmental impact and social responsibility. Companies that cannot demonstrate robust oversight risk reputational damage and may face exclusion from ESG‑focused investment portfolios. Moreover, large customers and insurance carriers often require evidence of continuous TPRM practices before awarding contracts or coverage.
1.3 Static vs. Real‑Time TPRM – A Comparison
The table below summarises key differences between traditional, static TPRM and modern, real‑time TPRM. Short phrases are used to make the comparison easy to scan; detailed explanations follow in subsequent sections.
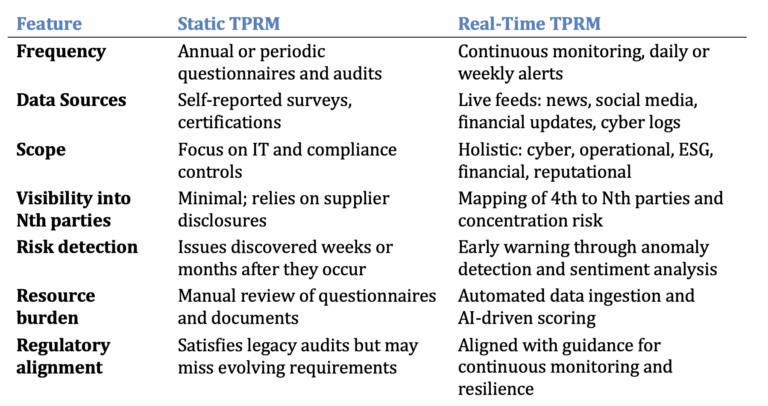
Static TPRM tends to be reactive and compliance‑focused; real‑time TPRM is proactive and risk‑based. Moving from the former to the latter requires new technologies, processes and mindsets, which we explore next.
Current Challenges and Trends in Third Party Risk Management
2.1 Continuous Monitoring Defined
In the context of TPRM, continuous monitoring refers to the process of automatically collecting and analyzing data about third parties on an ongoing basis. Rather than waiting for the next audit, risk management systems ingest streams of information financial statements, network telemetry, threat intelligence, news feeds, social media sentiment, legal filings, weather events and more, to evaluate how a vendor’s risk profile changes over time. Machine learning models detect anomalies, compare vendors against benchmarks, and generate alerts when risk thresholds are crossed. Continuous monitoring may still include periodic deep‑dive assessments, but these are targeted based on continuous signals rather than scheduled by calendar.
2.2 Regulatory Imperatives for Real‑Time Monitoring
Several regulatory initiatives explicitly call for real‑time or continuous oversight of third parties. As noted earlier, the U.S. Interagency Guidance emphasises that monitoring should be proportionate to the risk and may be periodic or continuous. It lists typical monitoring activities, such as reviewing financial statements, testing business continuity plans, assessing security incident reports, and verifying compliance with contractual obligations. The guidance also highlights the need to track external events, natural disasters, geopolitical shifts, and supplier workforce changes that may affect a vendor’s ability to deliver.
Europe’s DORA, effective 17 January 2025, mandates that financial institutions monitor their information and communication technology (ICT) providers for financial, ESG and cyber risks on an ongoing basis, not just at onboarding. Institutions must map fourth‑party dependencies and register information about each provider, including breach histories and adverse media records. The UK’s new rules for critical third parties align with DORA and require designated providers to carry out resilience testing, provide regular assurance and notify regulators of significant incidents. Australia’s APRA CPS 234 similarly requires organizations to continually test and improve their information security controls and to notify the regulator of material breaches. To comply with these overlapping regimes, firms must adopt monitoring solutions that can collect, analyze and report on diverse risk metrics in near real time.
2.3 Managing Fourth‑Party and Concentration Risks
The shift to continuous monitoring is driven not only by cyber‑security but also by the complex, multi‑tiered nature of supply chains. Fourth‑party risk occurs when your direct vendor relies on its own vendors. Mapping these relationships is challenging because information is often proprietary; yet failing to do so can hide critical dependencies. Industry experts emphasize that accurate, current supply‑chain and sourcing data is essential for identifying 4th to Nth‑party relationships and for understanding the roles and data handled by each provider. Concentration risk arises when many of your vendors depend on the same subcontractor or region. For example, if half of your suppliers rely on a single cloud provider or manufacturer, a local outage or political crisis could simultaneously disrupt multiple services. Recognizing these hidden interdependencies and assessing their cumulative impact is vital for operational resilience and regulatory compliance.
2.4 Visualizing a Real‑Time TPRM Ecosystem
To illustrate how real‑time monitoring works, the diagram below depicts a TPRM ecosystem powered by AI. On the left, multiple data sources, including financial data, cybersecurity events, compliance and ESG metrics, and social media or news feed,s flow into a central AI engine. The AI engine uses machine learning and natural language processing to ingest, normalize and analyze this data. It then produces risk scores and alerts that are sent to risk managers, compliance teams or automated workflows. This continuous feedback loop replaces the stop‑and‑go rhythm of annual questionnaires and ensures the organization is always aware of emerging supplier risks.
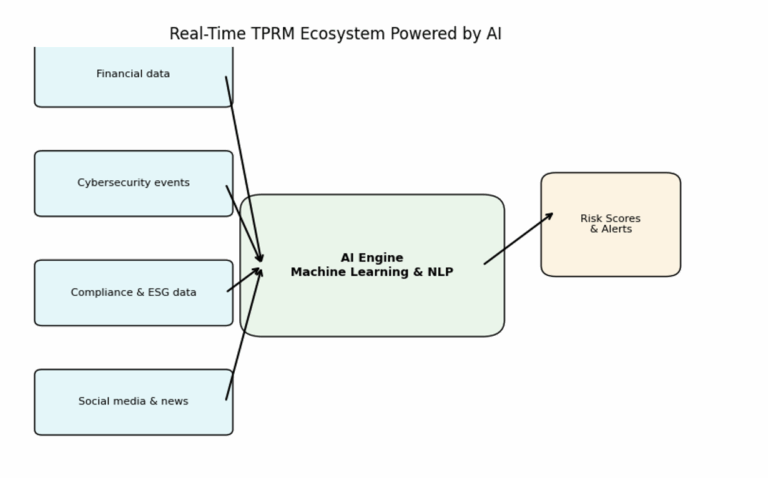
Figure 1: Real‑time TPRM ecosystem. AI ingests data from financial systems, cyber telemetry, compliance/ESG feeds and external news, generating risk scores and alerts in real time.
The AI engine is not a single magic box. It may include modules for sentiment analysis (to scan social media and news for adverse media), anomaly detection (to spot unusual network behaviour or transaction patterns), contract analytics (to extract obligations and performance metrics from legal documents) and predictive modelling (to estimate the likelihood of default or breach). Each module contributes signals to a unified risk score that can be tailored to the organization’s risk appetite and regulatory obligations.
2.5 Benefits of Continuous Monitoring
Continuous monitoring offers several benefits over static assessments:
- Early detection of issues. Real‑time data feeds allow organizations to catch incidents shortly after they occur, giving more time to respond and mitigate. For example, sentiment analysis of news and social media can alert teams to negative press or protests involving a supplier.
- Dynamic risk scoring. Risk scores can adjust as new information arrives, reflecting the current risk level rather than last year’s snapshot. This helps prioritize remediation efforts and allocate resources effectively.
- Proactive engagement. Instead of waiting for the next audit, risk managers can contact suppliers immediately when alerts fire, fostering a collaborative approach to remediation and improvement.
- Audit readiness. Continuous monitoring solutions typically maintain logs, reports and dashboards that simplify regulatory reporting and audits. Demonstrating ongoing oversight supports compliance with DORA, APRA, FCA/PRA and other frameworks.
- Integration with procurement and performance management. Real‑time data can feed into procurement platforms, contract management systems and supplier scorecards, aligning risk insights with operational decisions.
Of course, continuous monitoring also raises challenges: data quality and completeness, false positives, alert fatigue, and the risk of over‑reliance on AI. Addressing these requires careful tool selection, strong data governance and a balance of automation with human oversight.
How AI Transforms Vendor Due Diligence and Risk Scoring
Artificial intelligence is not simply a buzzword; it encompasses a set of technologies machine learning, natural language processing, knowledge graphs, anomaly detection, and generative models that can analyze huge volumes of structured and unstructured data faster and more accurately than humans. When applied to TPRM, AI transforms due diligence from a manual, document‑heavy process into a dynamic, data‑driven exercise. This section explores key AI capabilities and their impact on vendor risk management.
3.1 Automated Risk Scoring and Predictive Analytics
Traditional risk scoring often involves spreadsheets and manual weighting of questionnaire answers. AI enables automated risk scoring by ingesting diverse data (financial ratios, cyber‑security ratings, ESG scores, regulatory enforcement actions) and using supervised learning models to predict which vendors are most likely to experience a breach, default or compliance failure. An AI model might be trained on historical incidents to recognise patterns, such as a correlation between rapid expansion and control breakdowns or between adverse media mentions and subsequent sanctions. The model can then assign real‑time risk scores and adjust them as new information arrives. Such predictive analytics help organisations focus resources on high‑risk vendors and pre‑emptively remediate issues.
3.2 Natural Language Processing for Contract and Document Analysis
Vendor contracts, security policies, audit reports and ESG disclosures contain critical information but are often long and varied in format. Natural language processing (NLP) can extract key clauses (e.g., data‑breach notification requirements, subcontracting restrictions, service‑level agreements), detect missing terms, and flag obligations that need monitoring. NLP models can also compare vendor responses to security questionnaires against known frameworks (NIST, ISO, CIS) and highlight gaps. By automating document review, organizations reduce manual workload and ensure consistency, while risk managers can focus on exceptions and negotiation.
3.3 Anomaly Detection and Adverse Media Screening
AI algorithms are effective at detecting outliers in time‑series data. For example, if a supplier’s access logs show a sudden spike in failed login attempts, or if a payment pattern deviates from established norms, anomaly detection can trigger an alert. Likewise, unsupervised models can flag changes in sentiment or unusual patterns in news articles. Continuous adverse media screening monitoring newspapers, blogs, forums and social platforms for mentions of suppliers provides early warning of legal issues, fraud, human‑rights violations or reputational damage. Instead of manually reading thousands of articles, AI filters relevant content and summarizes key points for risk analysts.
3.4 Generative AI and Large Language Models
Generative AI, particularly large language models (LLMs), can further accelerate due diligence by drafting responses to vendor questionnaires, summarising lengthy documents, and answering open‑ended questions. In a case study from Greenlite (Grasshopper Bank), deploying a generative AI tool for enhanced due diligence reduced the time required by 70 percent, allowing the bank to scale client onboarding while maintaining compliance. LLMs can also translate documents from multiple languages, extract key facts, and create conversational interfaces for risk analysts. However, generative models must be carefully governed to avoid hallucinations, privacy breaches and bias. Human review remains essential to validate outputs and make decisions.
3.5 Intelligent Questionnaire Completion
Many risk management platforms now offer AI‑powered questionnaire automation. Instead of manually completing dozens of overlapping security questionnaires, vendors can upload their SOC 2 reports, ISO certificates or ESG audits, and the system uses NLP to extract the relevant answers and auto‑populate the forms. According to AuditBoard, such tools dramatically reduce the time vendors spend answering assessments and help organizations collect consistent data. AI can also suggest missing controls or improvements, and risk managers can tailor questions based on dynamic risk factors instead of using one‑size‑fits‑all surveys.
3.6 Integration Across Systems
AI‑enabled TPRM often requires integration with existing IT infrastructure: procurement systems, contract management platforms, enterprise risk management software, and SIEM (security information and event management) tools. Automated discovery functions can detect new vendors by connecting to accounts payable, procurement, or HR systems and trigger an onboarding assessment whenever a new supplier is added. Data can then flow bidirectionally: risk scores inform procurement decisions, and procurement data (e.g., spend, usage) enrich risk models. Over time, the organization builds a comprehensive vendor profile that includes financial, cyber, ESG and operational metrics, enabling more informed renewal or termination decisions.
3.7 Real‑World Outcomes and ROI
The financial benefits of AI in TPRM are tangible. IBM’s 2024 Cost of a Data Breach Report found that retailers and consumer packaged goods companies using security AI and automation saved $1.9 million on average compared to those that did not adopt these technologies. Across all industries, organizations that use AI extensively for threat detection, prevention and response saved $2.2 million on average, while understaffed security teams paid $1.76 million more in breach costs. The bar chart below visualizes the relative cost of a data breach for organizations with and without security AI and automation.
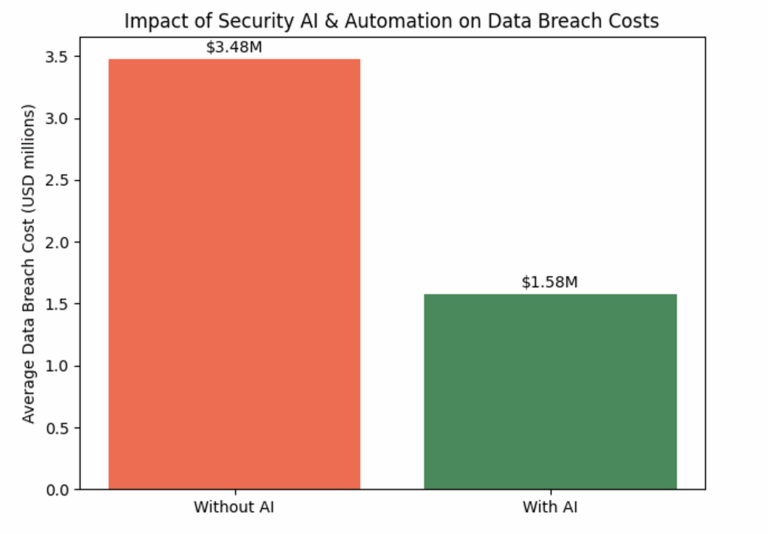
Impact of Security AI & Automation on Data Breach Costs
Figure 2: Average cost of a data breach in USD millions. Organisations that invest in security AI and automation experience significantly lower costs than those relying on manual processes. Data based on IBM’s 2024 Cost of a Data Breach Report.
In financial services, generative AI can reduce the time spent on enhanced due diligence by 70 percent. This not only lowers operational expense but also accelerates onboarding, enabling banks to serve more clients without increasing risk. Another advantage is improved accuracy: AI systems can process far more data points than human analysts and are less prone to overlooking subtle correlations. However, AI systems can also produce false positives or reinforce biases present in training data. Therefore, successful deployments pair AI with human expertise, robust data governance and continuous model validation.
Integrating ESG into Third‑Party Risk Management
Environmental, social and governance (ESG) considerations have moved from “nice to have” to central factors in vendor selection and monitoring. Investors, customers and employees expect companies to uphold sustainable and ethical practices not only internally but across their supply chains. Governments are also introducing mandatory ESG reporting and due diligence requirements, such as the EU’s Corporate Sustainability Reporting Directive (CSRD) and Germany’s Supply Chain Due Diligence Act. Integrating ESG into TPRM therefore supports both compliance and brand value.
4.1 ESG Risk Assessment and Due Diligence
According to Panorays, a strong ESG risk assessment should evaluate vendors’ environmental practices (carbon footprint, waste management, water usage), social responsibility (labour conditions, diversity and inclusion, community impact), and governance structures (board diversity, anti‑corruption policies, data governance) alongside traditional cyber, financial and compliance risks. Due diligence may involve reviewing sustainability reports, certifications (e.g., ISO 14001 for environmental management), and third‑party ratings; conducting site visits or interviews; and analyzing public disclosures and media coverage.
Importantly, ESG risk is ongoing, not just at onboarding. Companies should schedule regular audits, performance reviews and real‑time tracking to ensure that suppliers adhere to standards and improve over time. Detailed reporting helps document compliance and identify corrective actions. AI tools can support these efforts by scanning news for environmental incidents, monitoring social media for labour protests or community grievances, and alerting companies when a supplier’s ESG rating drops.
4.2 Challenges in ESG Integration
Integrating ESG into TPRM faces several challenges:
- Supply chain complexity and limited visibility. Large organizations may have thousands of suppliers spread across multiple countries. Collecting consistent ESG data for each is difficult, particularly for lower‑tier vendors. Panorays notes that mapping beyond the first tier and understanding who has access to sensitive data is a major obstacle.
- Data availability and accuracy. ESG metrics are less standardized than financial or cybersecurity metrics. Vendors may not collect certain data or may be unwilling to disclose it. Third‑party ratings can vary widely depending on methodology.
- Diverse regulatory environments. ESG regulations differ across jurisdictions. Companies operating globally must navigate a patchwork of laws and voluntary frameworks.
- Limited internal expertise. Many TPRM teams are staffed by compliance and security professionals who may not be familiar with carbon accounting, human‑rights law or anti‑corruption measures.
4.3 Best Practices for ESG‑Aware TPRM
The following practices can help overcome these challenges:
- Set clear ESG standards and communicate them to vendors. Incorporate ESG requirements into supplier contracts and onboarding documents. Mandate relevant certifications or adherence to recognized frameworks (e.g., Global Reporting Initiative, UN Guiding Principles on Business and Human Rights).
- Leverage technology for data collection and monitoring. AI‑based platforms can automate ESG data gathering, screen news and social media for incidents, and provide dashboards for tracking metrics. Integrate ESG signals into your overall risk score rather than treating them as an afterthought.
- Conduct regular audits and performance reviews. Schedule periodic assessments based on risk tier and use continuous monitoring to detect incidents between audits.
- Collaborate with vendors and provide training. Encourage vendors to improve their ESG practices by sharing resources, offering training, and building partnerships rather than just imposing penalties. A collaborative approach helps smaller vendors build capacity and fosters long‑term relationships.
- Align with procurement, sustainability and legal teams. ESG is cross‑functional; involves experts from sustainability, legal and procurement to ensure a holistic view.
By integrating ESG into TPRM, organizations can manage environmental and social risks, comply with emerging laws, and appeal to stakeholders who increasingly value responsible business practices.
Regulatory Drivers Shaping Modern TPRM
Regulators worldwide are codifying the need for continuous monitoring and resilience in third‑party relationships. Understanding these frameworks helps organizations design compliance‑ready TPRM programs. Below, we summarise key regulations and guidelines in major jurisdictions, along with practical implications.
5.1 United States: Interagency Guidance on Third‑Party Relationships
In June 2023, the Federal Reserve Board, the Federal Deposit Insurance Corporation (FDIC) and the Office of the Comptroller of the Currency (OCC) issued Interagency Guidance on Third‑Party Relationships. The guidance emphasises that banks must oversee third parties throughout the life cycle of the relationship, including planning, due diligence, contract negotiation, ongoing monitoring and termination. Key takeaways include:
- Ongoing monitoring should be commensurate with the level of risk and may be periodic or continuous. More critical services require more frequent review.
- Monitoring activities include tracking financial performance, reviewing internal controls, testing business continuity plans, assessing subcontractor management and verifying compliance with laws.
- Banks must maintain documentation of oversight activities and have clear escalation procedures when issues are identified. Contracts should ensure that banks have the right to audit and receive information.
Although the guidance targets banks, its principles are applicable to any regulated entity working with third parties. Organisations should adopt continuous monitoring tools and be ready to demonstrate their oversight to examiners.
5.2 European Union: DORA and the EU AI Act
DORA (Digital Operational Resilience Act) applies to banks, insurers, payment institutions, crypto‑asset service providers and other financial entities operating in the EU. Effective 17 January 2025, DORA requires firms to implement operational resilience frameworks, test their business continuity plans, and ensure ICT third parties meet the same standards. Among its key provisions are:
- Continuous monitoring of third parties for financial, ESG, cyber and breach risks.
- Mapping fourth‑party dependencies and maintaining a central register with firmographic information, breach history, adverse media and other risk data.
- Contract requirements that specify services, performance targets, locations of service delivery and security assurances.
Failure to comply can lead to fines and restrictions on outsourcing. Organisations operating in the EU should evaluate their TPRM technology for the ability to map fourth parties, track adverse media, and produce regulators’ requested reports.
In parallel, the EU AI Act represents the world’s first comprehensive law regulating artificial intelligence. It categorizes AI systems into unacceptable, high, limited and minimal risk categories and imposes strict obligations on high‑risk systems, including many used in financial services and critical infrastructure. Key points relevant to TPRM include:
- The Act has extraterritorial scope, meaning it applies to organizations worldwide that place AI systems on the EU market or use their output in the EU.
- Organizations must identify their role (provider, deployer, importer or distributor) and map and classify their AI systems.
- Third‑party AI providers must undergo rigorous due diligence to ensure compliance, including documenting training data, performance metrics and risk mitigations.
- Companies should incorporate AI Act requirements into contracts and conduct risk assessments focused on third‑party AI.
- The Act calls for internal policies on vendor management, acceptable AI use, data governance, incident response and AI literacy.
- The implementation timeline includes certain prohibitions and AI literacy requirements effective 1 February 2025, general purpose AI (GPAI) obligations and transparency provisions effective 1 August 2025, most provisions by 1 August 2026, and full enforcement by 1 August 2027. Organizations should plan compliance efforts accordingly.
The EU AI Act underscores that AI governance is not optional. Organisations using AI‑powered TPRM tools must ensure models are transparent, fair, non‑discriminatory and auditable. They should maintain records of data sources, model design, performance metrics and risk assessments, and create mechanisms for human oversight. Since the Act applies extraterritorially, non‑EU companies that serve EU customers or rely on EU data cannot ignore it.
5.3 United Kingdom: FCA/PRA Critical Third‑Parties Regime
In response to concerns about systemic concentration of outsourced services in a few providers (e.g., cloud giants), the UK government has empowered the Financial Conduct Authority (FCA) and Prudential Regulation Authority (PRA) to designate certain suppliers as critical third parties. From 1 January 2025, these CTPs must:
- Provide regular assurance and notifications to regulators about operational resilience.
- Undertake resilience testing, including joint exercises with firms and authorities.
- Report major incidents such as cyber‑attacks, natural disasters or power outages.
Importantly, the regime does not relieve financial institutions of their own responsibility to manage third‑party risk. Firms must continue to perform due diligence and monitoring; however, regulators will now have direct oversight of the most systemic providers. This underscores the need to coordinate TPRM programs with external testing and reporting frameworks.
5.4 Australia: APRA CPS 234
The Australian Prudential Regulation Authority (APRA) introduced CPS 234 to strengthen information security in regulated entities. Among its requirements, institutions must maintain an information security capability commensurate with the threat environment; implement controls and test them systematically; and notify APRA of material information security incidents. Continuous monitoring across the third‑party ecosystem is essential to comply. Third‑party risk ratings should cover cyber, operational and physical security, and institutions must ensure vendors meet baseline security requirements. Objective metrics, such as external security ratings from providers like Bitsight, can help demonstrate control effectiveness and support regulatory compliance.
5.5 Other Global Considerations
Regulatory harmonization remains incomplete. Companies operating across multiple jurisdictions must navigate overlapping and sometimes conflicting rules. For example, data privacy laws such as the EU General Data Protection Regulation (GDPR), California’s Consumer Privacy Act (CCPA) and Brazil’s LGPD impose obligations on data processing and cross‑border transfers that affect vendor management. Anti‑corruption statutes like the U.S. Foreign Corrupt Practices Act (FCPA) and the UK Bribery Act require due diligence on agents and intermediaries. Sector‑specific rules (e.g., healthcare, energy) further complicate the landscape. Keeping abreast of evolving regulations is therefore, an ongoing task and underscores the value of continuous monitoring platforms that incorporate regulatory intelligence.
The Return on Investment of AI‑Enabled TPRM
Investing in AI and continuous monitoring platforms can be costly up front, so executives often ask: What is the return on investment? Several sources demonstrate that the benefits outweigh the costs.
6.1 Hard Cost Savings: Avoiding Breaches and Fines
Data breaches and regulatory fines are expensive. The IBM data‑breach study found that retail organizations that extensively used security AI and automation saved $1.9 million compared to those with little or no AI. Across industries, the savings were $2.2 million on average. These savings stem from faster detection and containment of breaches; AI helps identify compromised accounts, suspicious transactions and malware behaviour before they cause widespread harm. The earlier an incident is detected, the cheaper it is to remediate. Moreover, continuous monitoring helps companies avoid regulatory penalties by demonstrating compliance and preventing violations.
6.2 Efficiency Gains and Resource Optimization
Manual due diligence is labour‑intensive. In the financial services case study cited earlier, a bank reduced enhanced due diligence time by 70 percent through generative AI. When questionnaires are automated and risk scoring is machine‑driven, analysts spend less time processing documents and more time investigating anomalies. Procurement teams receive timely risk insights and can accelerate contract negotiation and onboarding. Over time, the improved efficiency allows the TPRM program to scale without proportional headcount increases.
6.3 Improved Decision‑Making and Collaboration
AI provides a more comprehensive and accurate picture of vendor risk by combining cyber, financial, operational, ESG and reputational data. This holistic view supports better decision‑making: high‑risk vendors receive closer scrutiny, while low‑risk vendors move quickly through procurement. Cross‑departmental collaboration improves because risk scores and alerts are visible to procurement, finance, IT and legal teams, driving a shared understanding of priorities. Through integration with contract management systems, performance metrics can feed into renewal decisions and service‑level adjustments.
6.4 Intangible Benefits: Reputation and Resilience
Strong third‑party risk management enhances brand trust. Customers and investors are more likely to engage with companies that demonstrate diligence in selecting and monitoring suppliers. Over time, this can translate into higher revenues, lower insurance premiums and better access to capital. Continuous monitoring also builds operational resilience: early detection of vendor issues allows for contingency plans, alternative suppliers and business continuity measures. In the context of ESG, companies that proactively address environmental and social risks avoid reputational crises and can capitalize on the growing market for sustainable products.
6.5 Summary Table: Benefits of AI‑Enabled TPRM

These benefits provide a compelling case for investing in AI‑enabled TPRM. However, realising them requires careful implementation, as discussed next.
Roadmap for Modernising TPRM with AI
Implementing AI‑enabled, continuous TPRM is a multi‑year journey that touches people, processes and technology. The following roadmap outlines key steps to guide your transformation. Think of it as a professor describing a research project: systematic, iterative and grounded in evidence.
Step 1: Assess Your Current TPRM Maturity
Start by benchmarking your program against leading practices. How many vendors do you monitor? How often do you assess them? Which data sources and risk domains (cyber, financial, ESG, operational) do you cover? What tools and metrics do you use? Identify gaps relative to regulatory expectations (e.g., continuous monitoring, fourth‑party mapping, AI governance). Recognise that not all vendors require the same level of oversight; classify suppliers by risk tier to prioritize resources. Use maturity models or risk assessment frameworks to structure this evaluation.
Step 2: Build an Integrated Data Foundation
Continuous monitoring relies on timely, accurate data. Identify internal systems that hold relevant information (accounts payable, contract management, procurement, HR, incident management) and external sources (credit bureaus, ESG ratings agencies, threat intelligence feeds, news aggregators). Create a data lake or hub that consolidates these feeds in a consistent format. Define data quality criteria and establish governance processes for ingestion, cleansing and access control. Pay special attention to privacy laws (GDPR, CCPA) and ensure that data sharing with third‑party risk tools complies with consent and cross‑border transfer requirements.
Step 3: Select and Deploy AI‑Enabled Risk Platforms
There are numerous vendors offering TPRM platforms, security ratings, ESG analytics and AI toolkits. Evaluate these solutions based on functionality (risk scoring, contract analytics, fourth‑party mapping, regulatory intelligence), integration capabilities, transparency of algorithms, and track record. Consider whether you want a single end‑to‑end platform or a modular approach integrating specialized providers. Pilot the chosen solution with a subset of high‑risk vendors and refine based on feedback.
Step 4: Establish AI Governance and Ethical Frameworks
AI is powerful but must be used responsibly. Develop policies that define acceptable AI use, model lifecycle management, bias testing, explainability requirements, and human oversight. Document the data sources and features used in risk models and make them available for audit. Align your governance with external frameworks such as the EU AI Act, which requires providers and deployers of high‑risk systems to register them, conduct conformity assessments, maintain technical documentation and enable human review. Provide training for staff on AI literacy, ethics and bias mitigation, as mandated by the Act for certain organizations.
Step 5: Integrate Continuous Monitoring into Operations
Once your platform is running, integrate its outputs into daily operations. Define risk thresholds and escalation procedures: What constitutes a high‑priority alert? Which team receives which types of alerts? How quickly must suppliers respond? Connect risk scores to procurement approval workflows, vendor performance dashboards and contract management systems. Create feedback loops where vendor remediation actions update risk models. Use dashboards and analytics to identify trends, concentration risk, and systemic vulnerabilities.
Step 6: Coordinate with Regulatory and Compliance Teams
Ensure that your TPRM practices align with applicable regulations (DORA, FCA/PRA, APRA CPS 234, EU AI Act, etc.). Maintain documentation of monitoring activities, risk assessments and remediation actions. Prepare for audits by regulators or customers by generating reports and evidence through your monitoring platform. Engage legal counsel to review vendor contracts for compliance with new requirements such as DORA’s central register and fourth‑party mapping.
Step 7: Foster a Culture of Collaboration and Continuous Improvement
TPRM is not solely the responsibility of the risk department. Procurement, finance, IT, legal, sustainability and executive leadership all have roles. Establish a governance committee that meets regularly to review vendor risk profiles, emerging threats and regulatory changes. Encourage cross‑departmental education on cyber‑security, ESG, data privacy and AI ethics. Provide training to vendors and supply partners to help them meet your standards. Use metrics and benchmarks to evaluate the effectiveness of your program and adjust as needed. Just as scientific research evolves, so too must your TPRM approach; treat continuous monitoring as an ongoing experiment where hypotheses are tested and models refined.
Future Trends and Predictions
As we look ahead to 2025 and beyond, several trends will shape the future of third‑party risk management and AI:
8.1 Wider Adoption of AI in TPRM
Industry observers predict that adoption of AI for third‑party risk management will grow rapidly. A 2024 survey found that only around 5 percent of organizations were using AI in TPRM, but the number is expected to rise as firms seek predictive insights. The benefits of AI speed, accuracy, scalability are simply too compelling to ignore. Vendors will increasingly embed AI into their platforms, offering out‑of‑the‑box anomaly detection, risk scoring and continuous monitoring. At the same time, companies will invest in in‑house data science talent to develop bespoke models tailored to their industry and supply chain.
8.2 Tightening Regulations and Standardization
Regulatory frameworks such as DORA, the EU AI Act, and the UK CTP regime will become operational in 2025. Additional jurisdictions are likely to follow with their own rules on AI, cyber‑security, ESG and supply chain transparency. Over 80 percent of companies anticipate a significant impact of AI on risk and compliance within the next four to five years. To navigate this, industry associations and standard‑setting bodies may develop harmonized frameworks, and regulators may collaborate on joint testing exercises. Third‑party risk platforms that embed regulatory intelligence will become essential.
8.3 Expanded Scope of Risk Domains
TPRM has traditionally focused on cyber and financial risks. The future will encompass operational resilience, reputational risk, privacy, ethics and ESG. Real‑time monitoring will extend to physical infrastructure (e.g., remote facility conditions), climate‑related risk (e.g., suppliers’ exposure to extreme weather), and geopolitical developments. The integration of geospatial data, satellite imagery and climate models into risk scoring may become more common. AI models will need to account for these diverse data types while avoiding spurious correlations.
8.4 Responsible AI and Human Oversight
Concerns about AI bias, discrimination and lack of explainability are rising. Moody’s notes that while AI increases efficiency, it cannot work alone; human decision‑making remains crucial. Regulators and companies alike will require documentation of how models are built, what data they use, and how their outputs are interpreted. Explainable AI (XAI) techniques such as model scoring explanations and counterfactual analysis will become standard features of TPRM platforms. Organizations will adopt “human‑in‑the‑loop” processes where analysts review AI recommendations and make final decisions, balancing automation with accountability.
8.5 Greater Collaboration and Data Sharing
Risk cannot be managed in isolation. Just as scientists share data to accelerate discovery, organizations will share anonymized risk signals with industry peers, regulators and information‑sharing communities. This could include near real‑time feeds of supply chain disruptions, cyber‑threat indicators and ESG violations. Consortia may emerge to develop shared vendor risk databases that pool adverse incidents, ratings and compliance histories. Such collaboration raises privacy and antitrust concerns, but if done carefully, it can enhance collective resilience.
Frequently Asked Questions (FAQ)
Below are answers to common questions about modern third‑party risk management. Feel free to adapt these for your organization’s communications or training materials.
TPRM is the process of identifying, assessing and controlling risks associated with external entities that provide products or services to an organization. These entities may include suppliers, vendors, contractors, consultants, distributors and partners. Risk domains span cyber‑security, operational resilience, financial health, regulatory compliance, ESG and reputational impacts.
Static questionnaires provide a snapshot of a supplier’s controls at a single point in time. In today’s fast‑changing environment, a vendor’s risk profile can shift due to incidents, financial distress, geopolitical events or changes in subcontractors. Regulators such as the U.S. Interagency Guidance and Europe’s DORA expect ongoing monitoring. Continuous monitoring catches issues early and allows prompt remediation.
AI automates tasks like risk scoring, document analysis, anomaly detection and adverse media screening. It ingests structured and unstructured data from internal and external sources, applies machine learning to identify patterns, and generates alerts. AI reduces manual workload and improves accuracy. For example, generative AI cut due diligence time by 70 percent in a financial services case, and extensive use of security AI saved organizations up to $2.2 million in breach costs. However, AI must be governed responsibly and combined with human oversight.
Fourth‑party risk refers to the risk posed by your vendor’s vendors. Nth‑party risk extends this to any indirect supplier deeper in the chain. Without mapping these relationships, concentration risk can go unnoticed. For example, multiple vendors may rely on the same subcontractor, creating a single point of failure. Continuous monitoring helps identify and mitigate these dependencies.
Start by including environmental, social and governance criteria in your risk assessments and due diligence. Evaluate vendors’ sustainability reports, certifications and practices. Use AI tools to monitor news and social media for ESG incidents, conduct regular audits, and encourage suppliers to improve their performance. Align with emerging regulations such as CSRD and the German Supply Chain Act, and collaborate with procurement and sustainability teams.
DORA is an EU regulation aimed at strengthening digital operational resilience in financial services. It requires continuous monitoring of third‑party providers, mapping of fourth‑party dependencies and maintenance of a central register with breach history and performance data. If your organization operates in the EU or serves EU customers, you must ensure that your TPRM program meets these requirements by January 2025.
The EU AI Act is the world’s first comprehensive AI regulation. It classifies AI systems by risk and imposes obligations on high‑risk systems, including transparency, documentation, conformity assessments and human oversight. It applies extraterritorially to organizations placing AI systems on the EU market. The Act will roll out between 2025 and 2027. If you use AI in your TPRM or provide AI services to EU clients, you must evaluate whether your systems fall under the Act and plan for compliance.
Yes. AI enhances efficiency but cannot replace human judgment. Models may misinterpret data or inherit bias. Regulations like the EU AI Act emphasise human oversight and accountability. Analysts remain critical for making decisions, investigating anomalies, managing stakeholder relationships and interpreting complex or ambiguous events.
Conclusion: Building Resilient, Ethical and Future‑Ready TPRM Programs
Third‑party risk management is no longer a back‑office function confined to checklists and static questionnaires. In an era defined by digital interdependence, geopolitical uncertainty, ESG imperatives and sweeping regulation, TPRM must become real‑time, data‑driven and ethically grounded. AI, machine learning and natural language processing offer powerful tools to ingest diverse signals, detect anomalies and predict emerging risks. When combined with continuous monitoring, these technologies shift TPRM from reactive to proactive.
However, technology alone is not a panacea. Success requires strong governance, robust data management, human oversight and cross‑departmental collaboration. Regulators are making continuous monitoring mandatory, and the EU AI Act underscores the need for transparent and responsible AI. Organizations must plan their compliance roadmaps, train staff, and involve suppliers in building a resilient ecosystem.
The journey to modern TPRM is similar to a scientific research project: start with a clear hypothesis (e.g., that real‑time monitoring reduces risk), gather and clean data, select and validate models, test and iterate, and publish results to stakeholders. The process is continuous, with each cycle improving the accuracy of risk insights and the resilience of the organization. By embracing these principles today, companies can protect themselves from vendor‑driven shocks, meet regulatory expectations, and create trust with customers, investors and employees.
As you proceed, remember that risk management is a shared responsibility. Engage your suppliers, colleagues, regulators and peers. Use AI as an enabler, not a replacement for human expertise. And keep learning because just as science evolves, so too will the threats and opportunities in the world of third‑party risk.
Recent Blogs
Become a certified risk professional. Check our certificate programs:
- Certified Third Party Risk Management Professional (C3PRMP)
- 3PRM: Essentials in Third Party Risk Management
- 3PRM: Third Party Cyber Security Risk Management